In such environments, tracking headers means monitoring either directly within the server process (difficult in clouds), or within the client process (typically a browser).
Recently I had to reverse-engineer the convoluted authentication to the CMIS endpoint of a Sharepoint server. Below is my tale, and the tools I tried (spoiler: only the last one did the job).
Contestant 1: Chrome Developer Tools
In Chrome, I start Incognito mode (CTRL-SHIFT-N) to make sure no saved passwords/cookies interfere, fire up the Developer Tools (CTRL-SHIFT-I), select "Network" to see the requests, and launch the request.As seen in the screenshot below, Chrome shows the conversation between client and server. Something sounds fishy: Only 2 requests, and the last one is marked as "canceled" even though download succeded... let's try another tool!
Contestant 2: Firefox Web Console
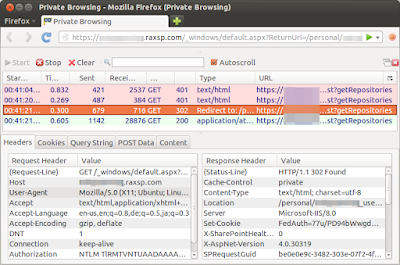
In Firefox, I start Private Browsing mode (CTRL-SHIFT-P), fire up the Web Console (CTRL-SHIFT-K), unselect everything but "Net", and launch the request.Firefox wins over Chrome by showing the right number of requests (four):
I click on a request, and something awful happens: a totally unusable window appears, displaying what I need (request headers and response headers), but preventing me from copy-pasting it.
Mouse selection goes crazy, and copying everything results in an unusable long string containing everything aggregated without spaces [1]. Not to mention the inexact timestamp [2], the content that does not scale with the window [3], and the weird titles font style [4].
Winner: Httpfox
In Firefox, after having installed the Httpfox extension, I start Private Browsing, fire up Httpfox (SHIFT-F2), press "Start", and launch the request.The lower part shows the headers, and copying them is accessible via the context menu... perfect!
If you know any other convenient tool, please let us know in the comments!
Nicolas Raoul



No comments:
New comments are not allowed.